Game Cracking Software
A Little History of DOS Games Cracks
Computer piracy has been around since the dawn of the home computer era in the late 1970s. Cartridge-based games systems were almost 100% free of piracy due to sheer cost of manufacturing the cartridges themselves. In fact, a blank cartridge was the vast majority of the outlay you paid to buy a game.
When 8-bit home computers came around in the early 80s, we typically saved and loaded to audio cassette, and since these were cheap to buy in blank form, copying original media became prevalent. This caused manufacturers to get creative in order to prevent their valuable IP from being stolen by the masses, including writing special loaders that would fool disk copying software programs from working properly.
In the really early days of DOS and the IBM PC, the same challenges faced both games and commercial software houses.
PC Booters
Some games would come on special floppy disks that you would boot directly into - these are often referred to as 'PC Booter' titles. They required no operating system in order to run, interacting with the PC and its graphics card at the BIOS level. One major advantage to this approach was that the program could be written knowing no other programs were present with which it had to share resources, and it could use all the memory the system had.
In most cases, these disks would not be readable if you first booted into DOS and tried to get the directory listing - the reason being, these disks were usually formatted with a different number of tracks and/or sectors per track than a standard DOS-formatted disk - DOS would simply interpret it as a defective disk.
As we approached the late 80s, hard disk prices were falling, and were now in reach of the home user. Because of this, installing software onto your hard disk was preferable; something not possible with a PC booter, as the files just weren't there to copy. Nobody wanted to keep a bunch of floppy disks next to their computer just to play a game - they wanted everything to be on their expensive hard disk. This eventually led to the phasing out of PC booters.
For a list of the PC Booters known to DOS Days, click here.
Key Disks
Other titles during the mid-to-late 1980s were not bootable (they required an operating system to be loaded first), but came with a 'key' disk, which was slightly different to a typical disk. The game would check for the presence of the key disk in your floppy drive before allowing the program to run.
These types of disk would not work on your copy if you copied them by just using the DOS DISKCOPY command. While DISKCOPY does a track-for-track, sector-for-sector copy of the source disk to the target disk, this would be too easy. Reading the directory structure of your new copy would show that all the files were present, and their sizes match the original. What was missing in the copy was uniquely identifiable information that was stored somewhere else on the original (usually a 'hidden' sector) that DISKCOPY could not see.
Some examples of copy protection on key disks were:
- A "weak" bit on track 0
- A hole in the physical media at a specific track/sector (PROlok)
- Copy-protected track/sector
- Writing to a gap between two sectors (SUPERlok)
- Additional 'hidden' sector in a certain track, e.g. F-19 Stealth Fighter
With the "weak bit" type of protection, the game would read Track 0 / Side 0 / Sector 0 four times.
It would then compare the first 16 bytes of each sector read, and iIf bytes 12-15 are *the same* each time, the disk was rejected. Some examples of this:
Gauntlet used a weak bit on track 0 (unsure which sectors).
Lemmings that has weak bits on tracks 0 through 4. Sectors 1 through 9 have 512 bytes per sector, sector 10 has 256 bytes per sector and sectors 11 and 12 have 512 bytes per sector with a bad CRC (cyclic redundancy check).
A hole in the media was just that - a laser-cut hole in the magnetic disc itself. The software would look for this and attempt to write something to it. If the write returned an error it would be rejected, but if it read back the written data at that location successfully it would know the disk was a copy. Circumvention of this type of check would require a patch to the executable program, hook Interrupt 13h (disk access) and have it simulate the error when it attempted to read back the stored data. If your game or its manual tells you not to write-protect the original disk, it is possible it is employing this type of copy protection.
Copy-protected track/sector - not so much actually flagged as copy-protected, this method used a non-standard track ID or sector ID written at the start of the track or sector which would not be recognised by standard programs like DISKCOPY. At the start of every sector on a DOS-formatted disk you have a number of bytes used to identify that a new sector is coming up along with information on how to identify the sector - at the start, a number of "gap" bytes exist that allow for some tolerance in floppy disk controllers' timings. These are usually 4Eh, followed by some "sync" bytes that tell the controller that a sector ID followed by sector data is next. These are a bunch of 00h followed by three A1h bytes. The sector ID follows, which comprises FEh followed by the track number, side number, sector number and the size ID byte. In the case of a copy-protected sector the sector number might be, say, 84 instead of the usual 1 through 9 (in the case of a DS/DD floppy). Since utilities like DISKCOPY only write standard sector numbers ranging from 1 through 9, this sector number would be incorrect on the new copy. Also, sometimes not all of these sectors would use the standard DOS 512 bytes per sector written into the size ID byte. The software would look for these differences and if found the software would work.
Writing to a gap between two sectors (the "gap" bytes themselves) - this was employed by a copy protection scheme called SUPERlok. The protection scheme would write to the 80-or-so bytes of available space between sectors - an area of the disk that the floppy disk controller doesn't expect to see (or look for) data. A normal IBM floppy disk controller could not write to these gaps, so if the checking code looks for the data at these locations and it's not present it knows the disk is a phony. SUPERlok would also encrypt the main program's executable, and a "loader" .COM file would only decrypt the executable if the signatures it finds in the gap bytes exist on the media.
Additional 'hidden' sector - this was quite a common method. A standard 360 KB DS/DD diskette was formatted to have 80 tracks (40 on each side) with 9 sectors per track. This method added a sector to one of the tracks and in some cases stored a small 'watermark' on this sector. The software would read this sector and, if detected and the watermark was present, the program would run. One commercial example of this was Harvard Graphics which had the text "HGC" stored on a hidden sector. All the usual disk checkers would report nothing abnormal between the original disk and a copy because they would only be looking for 80 tracks, each with 9 sectors - no 10th sector (which would have been an incorrect sector length on any floppy).
An early example of a Key disk was Sierra Online's King's Quest II: Romancing the Throne.
In nearly all cases, if you wanted to create a duplicate of an original key disk, it required third-party disk formatting utilities to be able to format a custom disk layout and then copy the key disk's contents onto your freshly-formatted one.
Another choice available around the time was an 'Option Board' - a physical expansion card that you installed into your PC, and with associated software would be able to duplicate copy-protected disks. Several such options boards were:
- Copy II PC Option Board, Deluxe Option Board and Enhanced Option Board
- Trans Copy Option Board
Offline Copy Protection
Today's article has us fast forward several more years when games companies like Broderbund, Microprose, Electronic Arts and Westwood Studios were putting copy protection into their titles. Often this protection was 'manual-based' where you would be asked to enter a word on a certain page, line and word number in the game manual, but other times it would be a copy protection cardboard disc, or codewheel as they became known.

Their Finest Hour by Lucasfilm Games, with the all-important codewheel
If you had lost your game manual or the codewheel, or had come by the game through less than 100% legal channels, your gaming experience would be rather short-lived. In some cases, the game would still allow you to play, but in a very restricted way - others would simply dump you back to the DOS prompt.
In the case of codewheels especially, most game manufacturers made attempts to incorporate the use of them into the storyline so it didn't come across as being blatant copy protection. With Their Finest Hour: The Battle of Britain for example, the codewheel was used to tune your radio so you could communicate with HQ and get a heading on where the enemy aircraft are. You could still fly around but wouldn't find any enemy aircraft until you had tuned the radio!
Enter the murky world of game cracks...
Of course, cracking had been around for several years already on the home computer scene where individuals with odd names ("handles"?) would tweak the game files by adjusting a few bytes here and there to bypass the offending copy protection screen altogether, or to accept any input as the correct one, thus allowing the continuation of your gaming pleasure. Once the game had been successfully "cracked", the crack details would be posted up on a BBS or a cracked version of one of the game files would be uploaded.
In many cases you could crack the game yourself if you have the crack details. With the use of the DEBUG command (an external DOS command), it was a simple matter of loading part of the file into memory, running a search for a specific set of consecutive bytes, overwriting them with different values, and writing that back to the file. This was made more user-friendly through the use of third party disk editors, such as Norton Disk Editor, which first appeared in version 5.0 of the product.
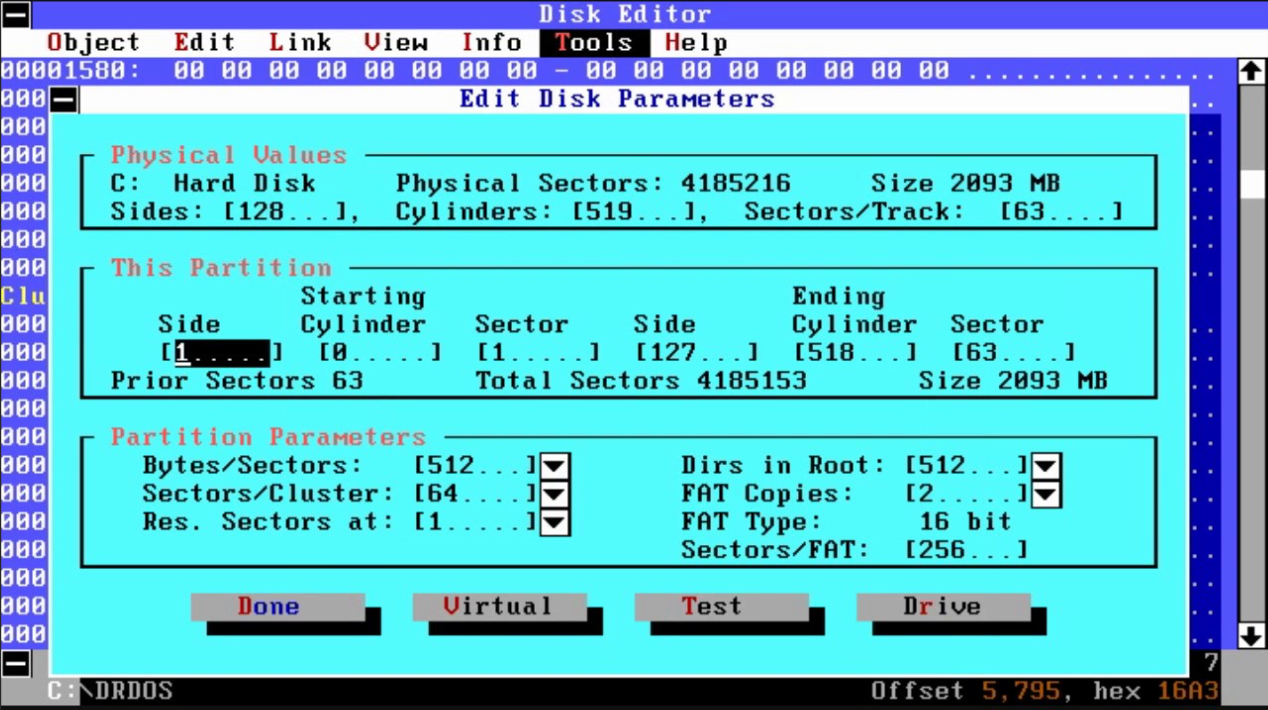
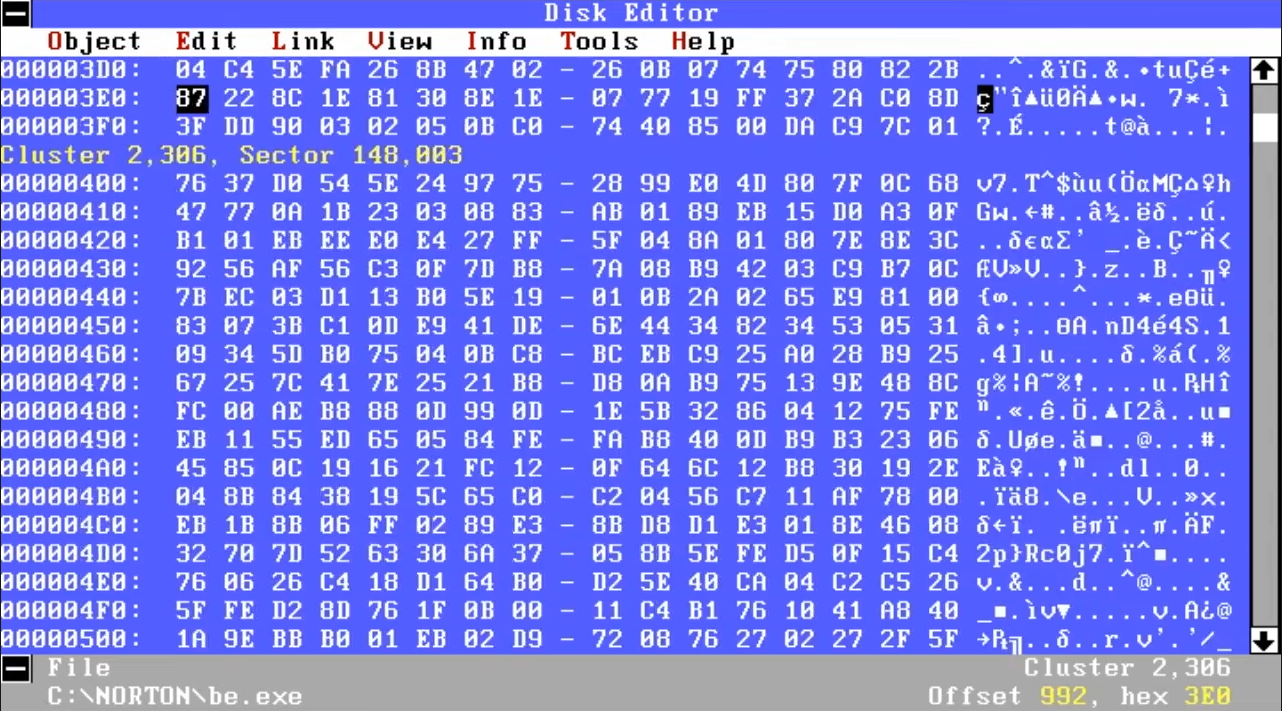
Norton's Disk Editor - dangerous in the wrong hands!
The use of such cracks was of course controversial, but these tools did contain legal warnings such as:
"<product> is intended solely for the use of legitimate owners or licensees of these products. If you are not a legitimate owner of a particular product that you wish to unlock, then STOP RIGHT NOW and go out and buy your OWN copy of the product."
and
"The sole intention of this software is to remove the annoyance of having to dig out your manual/code-wheel/key diskette everytime you want to play a game. Also for legimate purchasers of software who have mislaid their manual amongst all the other crap round their PCs. It is certainly NOT my intention, that anyone should use this software to make/distribute illegal copies of software. If you are using this program for this purpose, then you are very naughty indeed."
 I will add that all of the products we're going to dive into here were designed for legitimate use only by owners/licensees of the software to be cracked, and by using the tool to defeat the copy protection mechanism, you did so to take the annoyance of being asked for proof you own the original game. In my case, I have added images to these pages as evidence that I own the original.
I will add that all of the products we're going to dive into here were designed for legitimate use only by owners/licensees of the software to be cracked, and by using the tool to defeat the copy protection mechanism, you did so to take the annoyance of being asked for proof you own the original game. In my case, I have added images to these pages as evidence that I own the original.
So there you have it. As mentioned, earlier cracks were typically made available to download from a BBS (Bulletin Board System), and these tended to be a single crack that would work on a single game. Later, other tools were developed that combined hundreds of cracks into a single product. To name but a few, we have:
- CrackAid
- Neverlock
- RawCopy
- Locksmith
The names say it all. Let's 'crack' on then... (yawn, Ed.)
Crack Aid v3.39
Crack Aid was developed by Rawhide of -=The Humble Guys=- in May 1993. It featured cracks for no less than 233 games titles. In each case, cracking the game was a simple as installing the game, running Crack Aid, choosing the drive followed by the game directory, and letting Crack Aid do its thing.
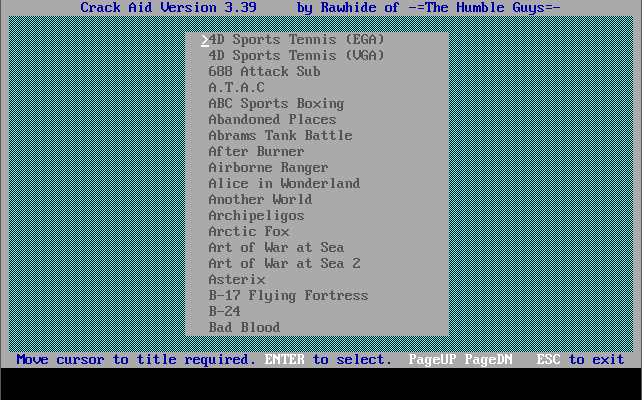
Crack Aid's game menu
Neverlock
Neverlock came out in Spring 1996, and comprises 264 games title cracks in its 'Classic Collection' menu, and a further 290 games title cracks in its 'Modern Collection' menu, making the total 554!
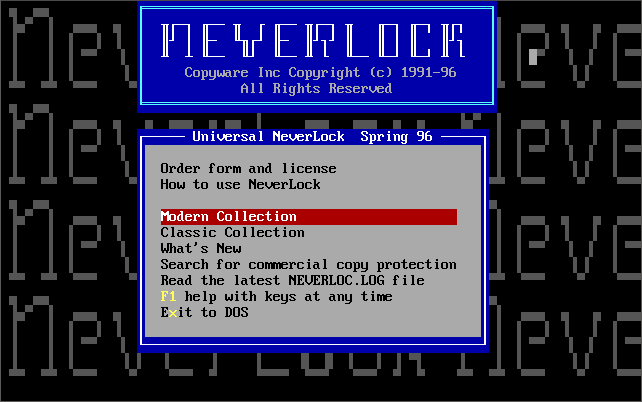

Neverlock Universal's main menu and the Modern Collection
Locksmith
Locksmith was created by a company called Omega Microware in Spring 1981. By 1987 they had gone out of business.
Disk Copying Utilities
Teledisk is a popular disk copying and imaging tool for DOS. One issue with it is that when it detects an unformatted track it will stop the copy. On the plus side, it runs even on very modern PCs.
Copy II Plus, written by Central Point Software and released in 1981, was one of the first copying tools that, when coupled with a special expansion card, the Option Board, could also duplicate some key disks. Copy II Plus was followed shortly after by Copy II PC, in 1982. The reception to these products and their ability to eliminate copy protection was met with horror - so much so that Central Point Software were driven out of the Software Publishers Association and the Wall Street Journal wrote a feature story on their president, Michael Brown, calling him "a hero to some, a villain to others." A Supreme Court case in 1984 settled the question of whether such software was "contributing to copyright infringement" declared that "as long as a product had a substantial noninfringing use, there was no contributory effect." The court also ruled that since copy-protection liberators (such as Central Point) give consumers the right to make archival copies which they are entitled to do under section 117 of the copyright law, the programs do have a substantial noninfringing use.
 Copy II PC was able to reproduce key disks, such as those that employed SUPERlok or similar. It also came with a utility called Nokey which fools any running software into thinking the key disk is inserted in Drive A:. It does this by monitoring any requests being made to the floppy drive, and upon detection sends back result codes to the program as if it had found the key disk.
Copy II PC was able to reproduce key disks, such as those that employed SUPERlok or similar. It also came with a utility called Nokey which fools any running software into thinking the key disk is inserted in Drive A:. It does this by monitoring any requests being made to the floppy drive, and upon detection sends back result codes to the program as if it had found the key disk.
CopyWrite, written by Quaid Software, was another group of utilities that outwit copy protection schemes. It's made up of the main utility CopyWrite, which can be used to reproduce copy-protected diskettes in full, UnGuard removes copy protection from the programs (mostly those protected with SUPERlok), and three more for use with more difficult copy protection: ZeroDisk, RamKey and SoloBoot. These allow you to run programs without using a key disk and are memory-resident.
Disk Mechanic by MLI Microsystems was a complex but feature-rich set of utilities, broken down into track/sector tools, file tools, and backup/copy/analyze/format tools. The latter took 3 separate approaches to defeating copy protection: A copier, plus special versions of CopyWrite and UnGuard from Quaid Software. NoLok is the same as Quaid Software's RamKey.